FIDO2 Authentication Error. "The relying party ID is not a registrable domain suffix of, nor equal to the current domain."
Using the Firefox browser you might receive the error "The operation is insecure".
The Fido2 server has many different settings you can use to change the Fido2 behavior. All of the Fido2 server settings are specified in the appsettings.json file located in the Fido2Server folder.
The probably two most important section is the V2 section which is for Fido2 set-up parameters.
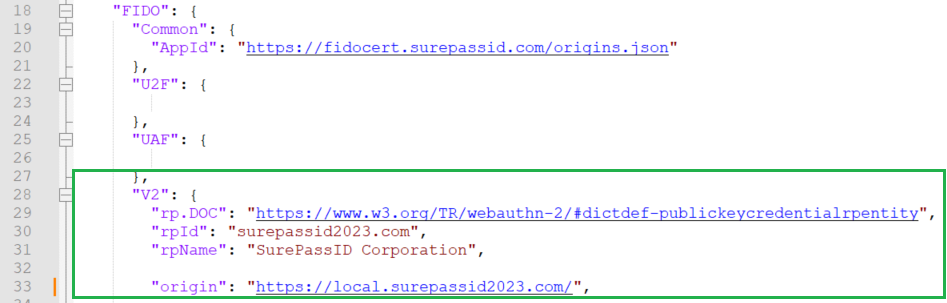
To properly set up the Fido2 server, you will need to specify certain parameters such as rpId, rpName, and origin. These parameters play a crucial role in ensuring the security and functionality of the Fido2 server. If you're wondering about the meaning of "relying partner" in webauthn terminology, you can refer to the webauthn relying party definition provided in the standard. Understanding this concept is important as it helps you grasp the role of the relying party in the authentication process.
According to the webauthn specification, the rpId refers to the Relying Party Identifier. It is used to define the scope of use for the tokens that are registered with the relying party. The relying party is responsible for saving the public key associated with the registered token's private key, which will be used for later authentication. On the other hand, the rpName is the user-friendly name of the relying party that will be displayed to the user during the token registration or authentication process. In most cases, it is recommended to set the rpId as your company's root domain name, such as mfa.goodcompany.com, and the rpName as your company's name.
The origin parameter in the Fido2 server settings specifies the domains that are allowed to make webauthn requests. For example, if you set the origin as local.goodcompany.com, only web apps with a URL of local.goodcompany.com or a higher level of fully qualified domain name (FQDN) like server1.local.goodcompany.com will be able to make webauthn requests. However, using a URL like server1.goodcompany.com would result in a failure. The origin ensures that the webauthn requests are restricted to the specified domains that can be validated by an SSL cert.
To provide a starting point, you can configure the mfa server as https://mfa.goodcompany.com and then set the origin to https://mfa.goodcompany.com. Then the URLs for the SAML2 Identity Provider (IdP) could be saml2.mfa.goodcompany.com, and servicepass could be servicepass.mfa.goodcompany.com, and any other apps would be anyotherapps.mfa.goodcompany.com.
It is crucial to keep in mind that the origin specified in the Fido2 server settings must also align with the URL (origin) of the application website. Therefore, it is necessary to have a valid SSL certificate in place to ensure a secure connection and proper origin detection.
While it is not a common scenario, it is possible to have multiple Fido2 servers that can handle different combinations of rpId, rpName, and origin.